Introduction
Within This Page
Crash- and attack-resistant bollards are used to protect military and governmental buildings and domestic structures and areas of higher security levels. The choice of more robust bollards over those that are not impact resistant is based on site vulnerability assessments and risk analysis. (See UFC/ISC Security Criteria Overview and Comparison; Cost Impact of the ISC Security Design Criteria; Threat/Vulnerability Assessments and Risk Analysis.)
Non-attack-resistant and attack-resistant bollards represent radically different safe/secure response conditions. Non-attack-resistant bollards are "perceived impediments to access." Theirs is an "expectation of civility," directed primarily at drivers with prescriptions for traffic control. Traffic control, while not necessarily static in its design, adjusting as it often does to daily shifts in traffic patterns, nevertheless is predictable to those who traverse the maze of cityscapes on a daily basis. With the expectation of traffic control, the issue and design of safe/secure is more predictable. It's civilized! And, accordingly, bollard configurations are more predictable.
Contrasted with drivers who are civil and compliant with society's norms are those who plan or carry out acts of property destruction, incite terrorism, or cause the deaths of civilian, industrial or military populations. They are opportunistic, seeking for security system weaknesses and avoiding, where- and when-ever possible a facility's strengths.
Employing crash- and attack-resistant bollards in the security design involves choices from a diverse pallet of styles. It is this versatility that influences the discussion.
This Resource Page documents that the definitions of safety, security, and perimeter security design are fluid concepts; that changing threat, vulnerability, and risk assessments for any one situation can require implementation of different design scenarios. For instance, when high profile domestic industries perceive themselves to be threatened in a manner similar to that in military environments, then security design codes and standards warrant shifts from a static to a more dynamic and fluid design. Because of their versatility bollards are important participants in changing security design.
Description
The tasks in this Resource Page are threefold:
To describe the industrial scope, costing, impact resistance, and style variations of crash / attack-resistant bollards
To show how bollards coordinate with other security designs (e.g. zones, stand-off, CPTED, landscaping, etc.)
To illustrate the emerging issue of how perimeter security design incorporates bollards randomly as a tactic to quell the impact of asymmetric terrorism.
I. Scope of the Crash / Attack-Resistant Bollard Industry¹
Manufacturers and Models
| N Models in Market | N Manufacturers | |
|---|---|---|
| Inactive Bollards | ||
| Fixed-Deep Set | 37 | 13 |
| Removable-Deep Set | 41 | 10 |
| Fixed-Shallow Set | 41 | 10 |
| Fixed-Surface Set | ? | ? |
| Active Bollards | ||
| Automatic Retractable² | 39 | 14 |
| Manual Retractable³ | 10 | 15 |
| Turntable⁴ | 1 | 1 |
| Total | 169 | |
¹ Derived from a detailed spreadsheet inventory of 17-items describing each of the 169 models, compiled by David McGee, Concentric Security, LLC, Montgomery, Alabama ² Fully hydraulic, pneumatic, or electric, activated by push-button ³ Requires assisting mechanism: screw drive, internal gas propellant, or counter-weight ⁴ Hybrid design: bollards remain fixed on a rotating turntable
Model Costs
While the metrics used for stopping effectiveness of active or passive bollards are the same (see below), the differences between active and passive bollards are significant when they are compared on initial and life-cycle costs.
Inactive (Passive) Bollards
The installation time for all models shown in this table is two to three days.
| Rating | Equipment Cost¹ (x $1000) | Installation Cost¹ (% of equipment cost) |
K4² | 2.6 | 47 |
|---|---|---|
| K4³ | 3.5 | 50 |
| K12⁴ | 2.8 | 89 |
| K12⁵ | 3.5 | 77 |
| K12² | 3.7 | 40 |
¹ From unpublished communication; all single bollard units ² Shallow mount fixed bollard ³ Shallow mount removable bollard ⁴ Deep mount fixed bollard ⁵ Deep mount removable bollard
(Noticeably absent in the foregoing and next table is listing of K8 bollards. K8s, in recent times, and increasingly are being covered by K12 solutions.)
Active (Retractable) Bollards: Hydraulic, Pneumatic, Manual
Illustrative manufacturer's costs in 2009 for manual and automatic retractable crash-certified active bollards vary by K-level and number of bollards per unit:
The installation time for all models in this table is three to five days for equipment and another three to four days for wiring.
| DoS Rating | Equipment Cost (x $1000) | Installation Cost (% of equipment cost) 2009 data |
|---|---|---|
| K4 | 25 to 35 | 133 |
| K4 | 15 to 20 | 75 |
| K12 | 29 to 39 | 118 |
| K12 | 43.2 | 50–75¹ |
| K12 | ~100 | 20–30² |
| 2012 (unpublished) data; three-bollard units | ||
| K4³ | 21 | 63 |
| K4⁴ | 40 | 85 |
| K12³ | 23 | 64 |
| K12⁴ | 48 | 76 |
¹ 3 bollards ² 4 bollards ³ Manual Retractable ⁴ Hydraulic Retractable
Active (Retractable) Bollards: Electric
Following industry trends, the newest and now ascending innovation is the electric bollard design. Being all-electric, it avoids the waste of hydraulics, doing away with waste pumps, fluid reservoirs, and hydraulic hoses. Models cover the entire crash-resistance range, operating speed matches that of hydraulics, and installation and maintenance cost are reported to be lower. Specific manufacturer information is available at:
Continuing Costs
Retractable bollards, again compared to inactive bollards, come with a price that further exceeds front-end equipment and installation costs and adds significantly to total life-cycle costing. Additional or continuing costs include:
Safety. The potential for injury to barrier operators requires warning signs, lights, bells, and bright colors to make the presence of the barrier known, and these must be maintained. Additional costs are back-up power, emergency cut-off switches, and installation of safety options.
Security. Barrier location invites sabotage when they are left unattended in remote areas. Additional costs are for anti-tamper switches, tamper-proof screws, and roaming security guards.
Reliability. When properly maintained (an ongoing cost), barrier failure rate is less than three percent. Local staff, however, requires training by the manufacturer for everyday- type operations independent of contracted maintenance.
Maintainability. Maintenance contracts (inclusive of labor and parts) are an indispensible cost reducing down time and system vulnerability to penetration.
Environmental Challenges. Hinges, hydraulics, or surfaces with critical tolerances to weather conditions require added attention by local operators.
Metrics of Impact Resistance
Architects, engineers, security designers, and end users need to understand the changing terminology associated with selecting appropriate barriers to protect their vital assets. In 2009, ASTM produced a new standard for the perimeter security industry by issuing ASTM F2656, which replaced the Department of State (DoS) SD-STD-02-01—Vehicle Crash Testing of Perimeter Barriers and Gates, Revision A, March 2003. The new ratings bring into chronological alignment the iteration of standards historically used by the Department of State, the Department of Defense (DoD) and now ASTM. Of barriers that are attack/crash-rated, they can be either formally crash-rated or engineer-rated.
Crash-rated barrier systems have been crash-tested and certified by a participating independent crash test facility. The tests are set up to ASTM or DoS specifications. Barrier system installation must replicate the testing design foundation, bollard spacing and number, beam lengths, etc., to be considered crash-rated. Manufacturers will have a certification letter from an independent testing organization, stating the barrier has passed the ASTM/DoS requirements for a certain vehicle type/weight, speed, and penetration level. Manufacturers also provide a dimensional drawing of the "as-tested" barrier system.
Engineer-rated barriers are systems that have been designed and computer-analyzed but not crashed or certified to ASTM or DoS specifications. These barriers often are interpolated from empirical data received from the results of crash-rated systems. Computer simulation can also manipulate system variations. Engineer-rated systems can differ in terms of foundation dimensions, bollard spacing, and barrier heights and widths. Engineer-stamped drawings show individual changes that have met certain requirements, or certify designs as fully meeting the requirements.
The DoD and DoS publish updated lists of approved bollard and barrier vendors.
Knowing the threat vehicle, the velocity it is expected to attain, and the acceptable penetration distance provides the ability to select an appropriate barrier for site specific conditions around a facility. The variables considered for different test conditions include the following:
- Vehicle speed (from 30–60 mph, depending on the threat vehicle)
- Vehicle type (small passenger car up to heavy goods truck)
- Vehicle weight (2430 lbs to 65,000 lbs, depending on the threat vehicle)
- Condition Designation (based on threat vehicle and velocity, equivalent to K-rating in former State Department standard)
- Penetration distance (DoS's L-rating; ASTM's P-rating)
The three standards are summarized in the next table from which comes this example illustrating use of the ASTM standard, as the increasingly preferred metric:
A M30 P1 crash barrier is designed to stop a Medium Duty Truck (M) traveling 30 mph with a penetration distance of ≤ 3.3ft
| Standard | ASTM | DOS | DOD | DOS |
|---|---|---|---|---|
| F2656-07 | SD-STD-02.01, Rev A, March 2003 | SD-STD-02.01, Rev A, March 2003 With penetration allowance | SD-STD-02.01, April 1985 | |
| Vehicle Speed | (M) Medium-duty truck (15,000 lbs) M30 (30 mph) M40 (40 mph) M50 (50 mph) (C) Small passenger car (2,430 lbs) C40 (40 mph) C50 (50 mph) C60 (60 mph) (PU) Pickup truck (5,070 lbs) PU40 (40 mph) PU50 (50 mph) PU60 (60 mph) (H) Heavy goods vehicle (65,000 lbs) H30 (30 mph) H40 (40 mph) H50 (50 mph) |
Medium-duty truck (15 000 lbs) K12 = 50 mph K8 = 40 mph K4 = 30 mph |
Medium-duty truck (15 000 lbs) K12 = 50 mph K8 = 40 mph K4 = 30 mph |
Medium-duty truck (15 000 lbs) K12 = 50 mph K8 = 40 mph K4 = 30 mph |
| Penetration | P1 ≤1 m (3.3 ft) P2 1.01 to 7 m (3.31 to 23.0 ft) P3 7.01 to 30 m (23.1 to 98.4 ft) P4 30 m (98 ft) or greater |
Only <1m penetration allowed | L3 = 3 ft. or less L2 = 3 ft. to 20 ft. L1 = 20 ft. to 50 ft. |
L3 = 3 ft. or less L2 = 3 ft. to 20 ft. L1 = 20 ft. to 50 ft. |
| Notes | Penetration indicates the test vehicle's maximum dynamic distance of penetration after impact with the barrier. Typically, the dynamic distance is barrier face to the front of the cargo bed. The barrier penetration rating does not imply that a barrier will perform as rated in all site conditions, approach routes, and topography. Also, only single-specimen tests at a specified impact location are required by this test method, and therefore, not all points of impact can be tested and validated for the penetration rating. Other impact locations may respond differently. | |||
©2011 Concentric Security - All Rights Reserved
Style Variations among Bollards
Passive Upright Mount—Fixed
- Permanent solution to preventing unauthorized vehicular access
- Pier-Type Footing (or Continuing Grade Beam Footing)

Passive Upright Mount—Removable
- Internal or external locking systems
- Physical removal required
- High security versions, because of greater weight (300-1200 lbs.) will require heavy lifting equipment
- No locking mechanism is required due to the sheer weight of the bollard


Passive Shallow Mount Bollard
- Prefabricated in factory to meet specific site requirements
- Site specifications are ready to accept prefabricated single-to-multiple bollard units upon delivery by heavy-duty truck
- Unique in industry by allowing location over undisturbed utility—electrical, plumbing, communications—equipment that otherwise would be damaged by a deep-set vertical fixed or removable bollard


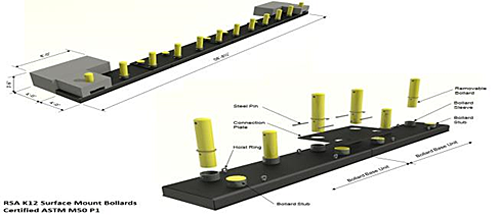
Passive Surface Mount
- This system is the newest addition to the bollard family and comes in K4 and K12 capacities (See examples at RSA Protective Technologies and Concentric Security, LLC).
- Its value is in its potential rapid random placement, although not yet shown as relevant to a RAM exercise (discussed below) because of size and weight. It can be deployed/removed/redeployed using heavy equipment and configured to local site configurations.

Active Retractable—Hydraulic/Pneumatic
- A proven product in the high security industry
- With proper maintenance provides years of service
- Uses environmentally friendly oil
Active Electric
- Higher in initial cost
- Reduced life maintenance and operational costs
- Because of longer-term lower life cycle costs, electric models are perceived as the future "state of the art design"

Active Retractable—Semi-Automatic
- Lesser cost with lack of external operating system
- Physical operation required of each bollard
- Drill-powered operation available on some models
- Internal hydraulic/pneumatic assisted, screw-drive mechanics
- Key-lockable


Active Retractable—Manual
- Least cost (among active styles) with exclusion of operating system
- Physical operation of each bollard required
- Key-lockable
Turntable Mount
- Cost: ~ $219K
- Installation time: ~ 2 weeks
- Operator or automatically controlled
- DoD rated K12
- Other details

II. Bollard Selection Based on System Design Applications
Current Applications
Security system design still is neither codified nor regulated, in the sense that no universal codes or standards apply to all public and private sector buildings. Government agencies (including all military services) and private sector organizations have developed numerous security design criteria. But these must be flexible and change in response to perceived emerging threats.
There are numerous standards related to perimeter security (see Resource Section). And there are just as many security system designs. Standards precede system design; design cannot be forced into a standard after the fact, an issue which has received attention, and recommends a sequence, similar to the following, leading to system design:
NEEDS DEFINITION
- Standards & Guideline Requirements
- Threat, Vulnerability, Risk Assessments
- Security Plan Development
- Stakeholder Input: Engineering, Intelligence, Security, Safety
THREAT DEFINITION
- Standards & Guidelines Requirements
- Threat Evolution
DESIGN
- Standards & Guideline Requirements
- Equipment (Bollard and Non-Bollard Options)
- (Bollard) Layout Options
This sequence is consistent with and informed by the WBDG guidance of Site Security Design Process, which proposes four hallmarks that must form the foundation of a successful and well-balanced security project:
- Strategic reduction of risk
- Comprehensive site design
- Collaborative participation
- Long-term development strategy.
These principles dictate the inclusion of crash- and attack-resistant bollards in any or all of their varieties and are illustrated by reference to GSA's Six-Zone Design and Landscape Architecture and the Site Security Design Process.
GSA's Six-Zone Design
By focusing on zones of the site, designers are able to better understand context and how the security elements (inclusive of bollards) in each zone contribute to element performance in the other zones. Several styles of bollards are used in the first three zones:
Zone 1—Neighborhood. Bollards can be used to
- Modify traffic conditions
- Be part of a total neighborhood security program
- Establish public right-of-way in the standoff zone
- Install temporary barriers for heightened levels of alert
Under usual risk conditions Zone 1 will be outfitted with non-crash rated bollards appropriate for traffic control. Under higher-threat conditions, crash-rated bollards can replace upright non-rated removable styles using the same receptacles or placed into receptacles reserved for random higher-threat conditions. (See Emerging Issues—discussion on Random Antiterrorism Measures-RAM.)
Zone 2—Standoff Perimeter. Bollards
- Provide a hardened perimeter where warranted, in conjunction with any of numerous other elements (sculptural barriers, walls, street furniture, fences, landscaping, etc.)
- Will all be crash-rated based on threat assessments and site design
Zone 3—Controlling Site Access and Parking.
- Retractable bollards in conjunction with inspection areas, gates, guard booths, and sally ports
- Removable crash-rated bollards, in conjunction with entry/exit roadways of straight, serpentine, or chicane design
In heightened alert situations, traffic access and egress can be randomly reconfigured by repositioning bollard combinations. (See Emerging Issues section.)
Bollard Versatility in Landscape Architecture Security Design
With the primary goal of minimizing loss of life of building occupants, the landscape architect assembles a multi-disciplinary team to address:
- Site planning
- Building configuration and location
- Setback distances
- Access control
- Parking
It does this to meet the all-important goal of "meeting security goals while preserving the ambience (values and ideals) of a free and democratic society".
Vehicular and pedestrian access. Tied to effective setback distance of vehicular access and circulation, bollards provide a protected space close to building entrances while allowing for drop-off areas for children, visitors, or disabled. The barriers' design effectiveness is measured by its prevention of straight-on lines of attack and breakthrough.
Bollards are used to prevent vehicles from leaving the roadway and circumventing efforts to restrict vehicular speed and circulation.
Parking. Surface parking areas are located to keep potential threats away from buildings, and, when bollards are used to border the perimeter of the parking area, they provide for a clear line of sight into it—a basic CPTED practice.
Security and landscape design. Bollards combine in streetscapes with other impediments to access (e.g., boulders, benches, water features, flagpoles, kiosks) to provide an aesthetically consistent extension to a building's safe zone.
Stand-off Distance. Distance in between blast and building is the most cost-effective approach to mitigate the effects of blast. Bollards define the required clear zone, which is free of visual barriers.
Physical Protective Barriers. Physical protective barriers consist of natural or manmade structures—changes in topography, vegetation, raised planted berms, fences, walls, planters, and bollards. These are employed in combinations or singularly.
Design Considerations for Vehicle Access and Entry Control. Provide traffic obstacles near entry points to slow traffic down, and offset vehicle entrances from the direction of vehicle approach to force speed reduction—both achieved with bollard-lined serpentine or chicane roadways. Vehicular access points (e.g., sally ports) should be augmented with retractable bollards.
Site Utilities. Whenever possible, site utilities should be placed underground. To do so, however, limits the use of structurally-upright bollards that can impair electric, communication, gas, and water conduits. The solution to this is to install shallow mount bollards over areas known to have underground utilities.
III. Emerging Issues
The foregoing discussion of site security design derives from three foundational phenomena: threat, vulnerability, and risk. These are the macro-dimensions on which engineers, intelligence experts, safety and security officers, and architects design protective systems.
It is notable that site designs take into account "clear lines of sight" to detect emerging threats. Crime Prevention Through Environmental Design (CPTED) generally and upright bollards specifically play a role here. These same lines of sight, however, also provide opportunity for those who seek to inflict damage to property or harm to personnel, thus altering prior measures of vulnerability, threat and risk and requiring renewed consideration of security design.
The terrorist attack cycle is a known process in terms of which attacks are carried out. These can be an early ally in behalf of the potential target's protective measures, involving security personnel trained in situational awareness and (the main interest here) choice and re-deployment of physical security elements and the bollard's role in that mix. The terrorist attack cycle is discernable and involves well known action points:
- Selecting or identifying the target
- Planning the attack, often concluding with a dry run and weapons acquisition
- Surveillance, requiring multiple efforts depending on target
- Operational or attack phase
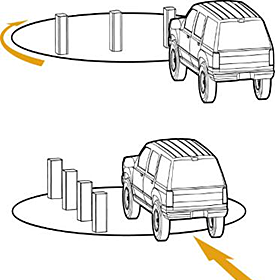
Random Antiterrorism Measures (RAM)
At some point during these steps (but primarily during the surveillance phase) the decision is reached to implement what has been described as the
Asymmetric threat: the terrorist's attempt to circumvent or undermine an opponent's strengths while exploiting his weaknesses, using methods that differ significantly from the opponent's usual mode of operation.
Adequate perimeter security measures, with their contingency plans, intend to turn this asymmetry on its head and be used against the terrorist using Random Antiterrorism Measures—RAM. Identified by military security experts as one of the best tactical measures to thwart terrorist attacks,
RAM is an asymmetric security response to asymmetric threats!
Rather than being sophisticated and invisible, those who conduct terrorist surveillance tend to be sloppy and even amateurish in their surveillance tradecraft. In this sense, they are detectable. The military takes advantage of terrorist surveillance by requiring all-personnel to undergo Awareness Training, and to implement Random Antiterrorism Measures (RAM). (See Air Force Instruction 10-245 AntiterrorismDownload afi10-245.pdf and Department of Defense Instruction 2000.16 DoD Antiterrorism StandardsDownload 200016p.pdf .
RAM is a critical element in site security design inclusive of bollard selection, and while originally a military tactic, it is becoming an all-site security practice for domestic settings, particularly high-value properties.
RAM supports the use of varying bollard patterns to disrupt terrorist surveillance operations. DoD's program proposes:
Random, multiple security measures that consistently change the look of an installation's force protection program. RAMs introduce uncertainty to an installation's overall force protection program to defeat surveillance attempts and make it difficult for a terrorist to accurately predict actions.
The U.S. NAVY definition is similar:
Random, multiple security measures that when activated, serve to disguise the actual security procedures in effect; RAMs deny the terrorist surveillance team the opportunity to accurately predict security actions. RAMs strictly vary the time frame and/or location for a given measure.
The discussion of RAM continues as part of a comprehensive perimeter security program in the concluding section.
The VBIED—The Terrorist's Weapon of Choice
Terrorism's Trojan Horse is the Vehicle Borne Improvised Explosive Device—capable of breaching undetected a security system or most other venues and delivering an explosive payload to unsuspecting enemy forces. If there is one attribute of terrorism that stands out it is the terrorist's weapon of choice ranging in weight from 2400 pounds up to heavy goods trucks of 65,000 or more pounds.
The DHS has defined the VBIED as a potential weapon of mass destruction, and it has proved itself as the weapon of choice in Iraq. START's Gary LaFree reports that, historically, the vehicle-borne explosive culprits were the Irish Republican Army, The Basque Fatherland and Freedom in Spain, the Taliban, and al Qa'ida in Mesopotamia. With this history to perfect the Trojan Horse, it now has shown up on the steps of America.
Mexican officials are raising concerns that Hezbollah operatives are training Mexican drug cartel enforcers in making car bombs. These car bombs show an evolution in cartel tactics, one evidence being an indictment handed down in mid-2010 by the Southern District Court in New York that showed a connection between Hezbollah—the proxy army of Iran—and drug cartels violently plaguing the U.S./Mexican border. And still more evidence being the cell-phone-detonated car bomb (the first of its kind) deployed just across the U.S.-Mexican border in Juarez.
What has been learned is that the threats in the hands of terrorists are purposefully designed to be asymmetric—circumventing or undermining strengths while exploiting weaknesses, using methods that differ significantly from the usual mode of operations.
It just so happens that the usual modes of operations, inclusive of codes and standards, are published and available to the public, terrorists included. Most industries and all military establishments, since 9/11, have published one or more security/engineering formulations, to include sections on perimeter security and site design. UFC 4-010-01 Security Engineering: Minimum Anti-Terrorism Standards for Buildings is a typical example and categorically addresses
- Standoff Distances
- Unobstructed Space
- Drive-up/Drop-off Areas
- Access Roads
- Parking Beneath Buildings or on Rooftops
Similarly, in Section 550 of the Homeland Security Appropriations Act of 2007 (P.L. 109-295) Congress gave DHS regulatory authority over security at high-risk chemical facilities to complete security vulnerability assessments, develop site security plans, and implement protective measures necessary to meet DHS-defined risk-based performance standards. Three of the actions focus on perimeter security:
- Restrict Area Perimeter: Secure and monitor the facility perimeter
- Secure Site Access: Secure and monitor restricted areas or potentially critical targets within the facility
- Screen and Control Access: Control access to the facility and to restricted areas within the facility by screening and/or inspecting individuals and vehicles as they enter
It should come as no surprise that terrorists most likely also have downloaded and apprised themselves of both UFC 4-010-01 and P.L. 109-295 (and of other guidelines as well), conducted their usual target surveillance to determine site vulnerability, and now merely wait for the best time to attack—asymmetrically.
To put it more succinctly, security experts have advertised these basic designs.
Cutting across all security standards and threat assessments, the engineering/security/intelligence/safety team has two resources to mitigate successful attacks:
- Random Antiterrorism Measures (RAM) strategy and tactics
- The recognized versatility of bollards that contribute to RAM
RAM is the fruit of the seasoned imaginations of engineers and security professionals to build unpredictability into the security design and function of valued facilities and their sites. Broadly defined examples amenable to RAM include
- Perimeter and standoff design
- Site and building vehicle and personnel access and egress
- Traffic directional and speed control patterns
- Vehicle and personnel delays, searches, and routings
- Calendar and time-of-day scheduling variations
These are joined in the following example of a RAM exercise:
Principle: Removable deep-set non-rated bollards allow traffic patterns to be changed, which hampers breach (access) and escape (egress). Increased threat conditions can warrant interspersing K4-12 bollards of similar style to reduce high speed approach of vehicles near high risk targets. While these measures can cause delay in traffic, the prevention of planning and surveillance efforts by terrorists are thwarted at the perimeter. (In military settings, the intensity of RAM increases relative to the perceived threat levels—Alpha, Bravo, Charlie, Delta.)
Access. Scenario–1
Under normal conditions during peak traffic hours, the bollards are removed to allow for maximum traffic throughput. A RAM would involve insertion of bollards during peak traffic for undisclosed periods. This slows traffic but varies traffic flow to disrupt usual patterns.
Access. Scenario–2
RAM also would limit the number of access lanes by using bollards to block off lanes:
- Monday, the inside lane is blocked
- Tuesday, the middle lane is blocked
- Wednesday, the outside lane is blocked
Access. Scenario–3
As traffic approaches an inspection portal (sally port), K-rated deep-set bollards on both sides of the lane will prevent last moment break-through to avoid inspection. On the exit side of the portal fully- or semi-automatic hydraulic or pneumatic bollards, rated K-4/K-8 will retract to allow entrance.
Egress. Scenario–4
Outbound/exit lanes would (1) all be open or (2) configured in a serpentine or chicane design. Random lane closures are used here for a RAM effect.
Conclusion
The Resource Page companion to this one on non-attack/non-crash resistant bollards introduced a way to see safety and security in tandem with each other. Safety is defined as the code- or standard-related "steady state" of some entity, i.e., it was doing what it was supposed to do. And security as the means that preserved, protected, or promoted that steady state when confronted by some natural or man made threat. On the basis of these two definitions one is able to arrive at operational definitions or performance-based measures of both concepts.
Contrasted with the rather sublime existence of traffic control bollards whose fate merely depends on sane and civil persons doing what they are supposed to do, crash- and attack-resistant bollards are designed to withstand deliberate wanton acts of destruction and death and the prolonged after-effects of terror.
The types, costs, and performance metrics of the bollards could have been cataloged in this Resource Page. But Asymmetric Threats targeting high-value properties—public and domestic—requires calculated responses to those who threaten. For this reason the surveillance stage of the terrorist life cycle is identified as requiring heightened awareness by potential target populations. This led to the tactical mixing and matching of bollard configurations known as Random Antiterrorism Measures, to confuse and render sterile would-be terrorists.
The result is a dynamic situation-relevant way to define and design perimeter security. Increasingly perimeter design must become a moving and adjusting response to a moving threat. If there is anything anti- and counter-terrorism experts have learned in recent years is that terrorists are opportunists who change their attack modalities to circumvent or undermine their opponent's strengths while exploiting his weaknesses using ever-changing methods that differ significantly from the opponent's usual mode of operation. As long as the VBIED is the preferred mode of destruction, RAM is relevant, and the cataloguing of bollards and their combinations aids in saving lives.
Relevant Codes and Standards
Department of Defense
- DOD Security Engineering Manual (For Official Use Only)
- FM 3-19.30 Physical Security—Sets forth guidance for all personnel responsible for physical security
- MIL-HDBK-1013/1A Design Guidelines for Physical Security of Facilities
- UFC 1-200-01 Design: General Building Requirements
- UFC 4-010-01 DoD Minimum Anti-Terrorism Standards for Buildings
- UFC 4-010-02 DoD Minimum Standoff Distances for Buildings (FOUO)
- UFC 4-020-01 DoD Security Engineering Facilities Planning Manual
- UFC 4-020-03FA Security Engineering: Final Design (FOUO)
- UFC 4-023-03 Design of Buildings to Resist Progressive Collapse
- GSA Progressive Collapse Guidelines
- GSA Occupant Emergency Program GuideDownload gsa_oepguide.pdf
Department of Veterans Affairs (VA)
- Physical Security And Resiliency Design Manual
- Physical Security Design Manual for VA Facilities: Cost Estimates for Physical Security Enhancements
Department of Homeland Security
- BIPS 05 Preventing Structures from Collapsing
- Colleges and Universities and the Chemical Facility Anti-Terrorism Standards (CFATS)Download cfats_cu_brochure.pdf
- Chemical Facility Anti-Terrorism StandardsDownload cfats_brochure.pdf
- Colleges and Universities and the Chemical Facility Anti-Terrorism Standards (CFATS) Fact SheetDownload cfats_cu_factsheet.pdf
- The Role of Emergency Responders in the Chemical Facility Anti-Terrorism StandardsDownload responders_cfats_brochure.pdf
Department of State
- Architectural Engineering Design Guideline (5 Volumes) (For Official Use Only)
- Physical Security Standards Handbook, 07 January 1998 (For Official Use Only)
- Structural Engineering Guidelines for New Embassy Office Buildings, August 1995 (For Official Use Only)
Federal Aviation Administration (FAA)
- FAA Order 1600.69 Security Risk Management
Federal Emergency Management Agency (FEMA)
- FEMA 386 Series on Mitigation Planning
- FEMA 386-7 Integrating Manmade Hazards into Mitigation Planning
- BIPS 06 / FEMA 426 Reference Manual to Mitigate Potential Terrorist Attacks Against Buildings
- FEMA 427 Primer for Design of Commercial Buildings to Mitigate Terrorist Attacks
- BIPS 07 / FEMA 428 Primer to Design Safe School Projects in Case of Terrorist Attacks and School Shootings
- FEMA 429 Insurance, Finance, and Regulation Primer for Terrorism Risk Management in Buildings
- FEMA 430 Site and Urban Design for Security
- FEMA 452 Risk Assessment: A How-To Guide to Mitigate Potential Terrorist Attacks Against Buildings
Perimeter Design
- Army Access Control Points Standard Definitive Design Guide
- UFC 4-022-01 Security Engineering: Entry Control Facilities/Access Control Points
- UFC 4-022-02 Selection and Application of Vehicle Barriers
- UFC 4-022-03 Security Engineering: Fences, Gates, and Guard Facilities
- UFGS 32 31 13.53 High-Security Chain Link Fences and Gates
- UFGS 34 71 13.19 Crash Rated Active Vehicle Barriers and Controls
Private Sector Guidelines
- ASCE/SEI 7-10 Minimum Design Loads for Buildings and Other Structures
- Design of Blast Resistant Buildings in Petrochemical Facilities, Second Edition by Amercan Society of Civil Engineers (ASCE). 2010.
- International Building Code (IBC) International Code Council (ICC)
- Structural Design for Physical Security, State of the Practice by Edward Conrath, et. al. Alexandria, VA: Structural Engineering Institute of American Society of Civil Engineers (ASCE), 1999.
Additional Resources
Websites
- Federal Emergency Management Agency (FEMA)
- Interagency Security Committee (ISC)
- The Infrastructure Security Partnership (TISP)
- Unified Facilities Criteria (UFC)
- U.S. Access Board
Security Centers
- Department of Defense (DOD) Anti-terrorism body—Pentagon's J34
- Federal Emergency Management Agency (FEMA) All-Hazard Mitigation Program on Anti-terrorism
- Naval Facilities Engineering Service Center (NFESC), Security Engineering Center of Expertise ESC66—E-mail: securityeng@nfesc.navy.mil
- USAF Electronic System Center (ESC), Hanscom AFB
- U.S. Army Corps of Engineers, Electronic Security Center
- U.S. Army Corps of Engineers, Protective Design Center
- U.S. Department of Defense
- U.S. Department of Homeland Security
Others
- 21st Century Security and CPTED by Randall I. Atlas, 2008.
- Creating Defensible SpaceDownload def.pdf by Oscar Newman. Washington, DC: U.S. Department of Housing and Urban Development, April 1996.
- Crime Prevention Through Environmental Design by Ray Jeffery, 1977.
- National Symposium of Comprehensive Force Protection, Society of American Military Engineers (SAME), Charleston, SC, Lindbergh & Associates, Oct 2001.
- NIST WTC Investigation: Building Standards and Codes: Who is in Charge?










