Introduction
Within This Page
Industrial Control Systems (ICS) are physical equipment oriented technologies and systems that deal with the actual running of plants and equipment, include devices that ensure physical system integrity and meet technical constraints, and are event-driven and frequently real-time software applications or devices with embedded software. These types of specialized systems are pervasive throughout the infrastructure and are required to meet numerous and often conflicting safety, performance, security, reliability, and operational requirements. ICSs range from building environmental controls (HVAC, lighting), to systems such as the electrical power grid. With the increasing interconnectivity of ICS to the internet, the ICS can be an entry point into the organization's other IT systems.
Within the controls systems industry, ICS systems are often referred to as Operational Technology (OT) systems. Historically, the majority of OT systems were proprietary, analog, vendor supported, and were not internet protocol (IP) enabled. Systems key components, such as Remote Terminal Units (RTUs), Programmable Logic Controllers (PLCs), Physical Access Control Systems (PACs), Intrusion Detection Systems (IDSs), closed circuit television (CCTV), fire alarm systems, and utility meters have become digital and IP enabled. OT systems use Human Machine Interfaces (HMIs) to monitor the processes, versus Graphical User Interfaces for IT systems. Most current ICS systems and subsystems are now a combination of Operational Technologies (OT) and Information Technologies (IT).
The Stuxnet, Duqu, Flame and Shamoon malware were specifically designed to target ICS and cause physical damage to the processes or equipment. Stuxnet "spoofed" the integrity of the uranium centrifuges and caused the centrifuges to overspin and self-destruct, while the operators console showed the system was operating within normal parameters. The Duqu malware looks for information that could be useful in attacking industrial control systems. Its purpose is not to be destructive; the known components are trying to gather information. The Flame malware looks for engineering drawings, specifications, and other technical details about the systems and records audio, screenshots, keyboard activity, and network traffic. The program also records Skype conversations and can turn infected computers into Bluetooth beacons which attempt to download contact information from nearby Bluetooth-enabled devices. The Shamoon attack destroyed over 30,000 Saudi Armco work stations. Shamoon is capable of spreading to other computers on the network, through exploitation of shared hard drives. Once a system is infected, the virus continues to compile a list of files from specific locations on the system, erase and then send information about these files back to the attacker. Finally, the virus will overwrite the master boot record of the system to prevent it from booting as shown in Figure 1.
Figure 1: The Shamoon malware has the ability to overwrite the master boot record of a computer.
Image credit: Securelist
In March 2018, the Department of Homeland Security issued Alert (TA18-074A) Russian Government Cyber Activity Targeting Energy and Other Critical Infrastructure Sectors.
"This alert provides information on Russian government actions targeting U.S. Government entities as well as organizations in the energy, nuclear, commercial facilities, water, aviation, and critical manufacturing sectors. It also contains indicators of compromise (IOCs) and technical details on the tactics, techniques, and procedures (TTPs) used by Russian government cyber actors on compromised victim networks.
This campaign comprises two distinct categories of victims: staging and intended targets. The initial victims are peripheral organizations such as trusted third-party suppliers with less secure networks, referred to as "staging targets" throughout this alert. The threat actors used the staging targets' networks as pivot points and malware repositories when targeting their final intended victims.
In multiple instances, the threat actors accessed workstations and servers on a corporate network that contained data output from control systems within energy generation facilities. The threat actors accessed files pertaining to ICS or supervisory control and data acquisition (SCADA) systems."
Figure 2 shows how DHS was able to reconstruct screenshot fragments of a Human Machine Interface (HMI) that the threat actors accessed.
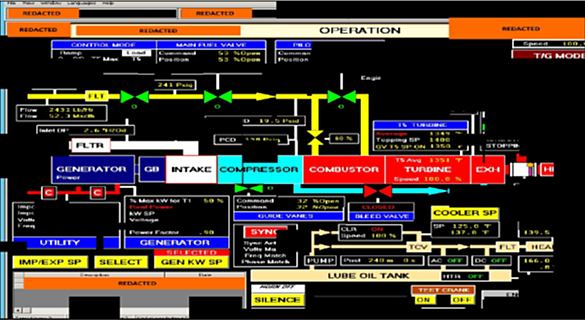
Figure 2: Reconstructed screenshot fragments of a Human Machine Interface (HMI) that the threat actors accessed.
Photo Credit: www.us-cert.gov/ncas/alerts/TA18-074A
In February 2013, Executive Order Improving Critical Infrastructure Cybersecurity was issued which requires the National Institute of Standards and Technology (NIST) to "lead the development of a framework to reduce cyber risks to critical infrastructure (the "Cybersecurity Framework"). The Cybersecurity Framework shall include a set of standards, methodologies, procedures, and processes that align policy, business, and technological approaches to address cyber risks. The Cybersecurity Framework shall incorporate voluntary consensus standards and industry best practices to the fullest extent possible.
While federal agencies have been required to meet stringent Cybersecurity standards for the traditional IT systems since the Federal Information Security Management Act (FISMA) was passed in 2002, the same level of protection and analysis is just beginning to be developed for building control systems. Buildings are becoming increasingly reliant on technologies that allow centralized monitoring and control of multiple building systems ( Building Automation, Fire and Life Safety, Energy Management, Physical Security, Access Control, etc.), to assist in accomplishing design and operational goals. Because of the unique operating and configuration of building control systems, traditional IT processes such as continuous monitoring, host based scanning, and automated patch management can cause building control systems to fail or become non-operational.
This section will provide an overview of the current efforts underway with regards to policy, standards, guides, and tools to assist building owners and operators, designers, and constructors meet the Cybersecurity challenges.
Description
Industrial Control Systems and Operational Technology
Within the controls systems industry, Industrial Control Systems (ICS) are often referred to as Operational Technology (OT). ICS are physical equipment oriented technologies and systems that deal with the actual running of plants and equipment, include devices that ensure physical system integrity and meet technical constraints, and are event-driven and frequently real-time software applications or devices with embedded software. These types of specialized systems are pervasive throughout the infrastructure and are required to meet numerous and often conflicting safety, performance, security, reliability, and operational requirements.
NIST SP 800-53 R4 defines ICS as:
An information system used to control industrial processes such as manufacturing, product handling, production, and distribution. Industrial control systems include supervisory control and data acquisition (SCADA) systems used to control geographically dispersed assets, as well as distributed control systems (DCSs) and smaller control systems using programmable logic controllers to control localized processes.
NIST SP 800-82 R2 further expands on the characteristics of ICS:
Although some characteristics are similar, ICS also have characteristics that differ from traditional information processing systems. Many of these differences stem from the fact that logic executing in ICS has a direct effect on the physical world. Some of these characteristics include significant risk to the health and safety of human lives and serious damage to the environment, as well as serious financial issues such as production losses, negative impact to a nation's economy, and compromise of proprietary information. ICS have unique performance and reliability requirements and often use operating systems and applications that may be considered unconventional to typical IT personnel. Furthermore, the goals of safety and efficiency sometimes conflict with security in the design and operation of control systems.
The term ICS is used in its broadest sense which includes:
- Supervisory Control and Data Acquisition (Energy, Water, Wastewater, Pipeline, Airfield Lighting, Locks, and Dams, etc.)
- Distributed Control Systems (Process and Manufacturing, etc.)
- Building Control Systems/Building Automation Systems
- Utility Management Control Systems
- Electronic Security Systems
- Fire, Life Safety, Emergency Management Systems
- Exterior Lighting and Messaging Systems
- Intelligent Transportation Systems
Within the Department of Defense, there are over 30 unique types of ICS as shown in Figure 3. There are an estimated 2.5 million unique ICS systems that are used in over 300,000 buildings and over 250,000 linear structures.
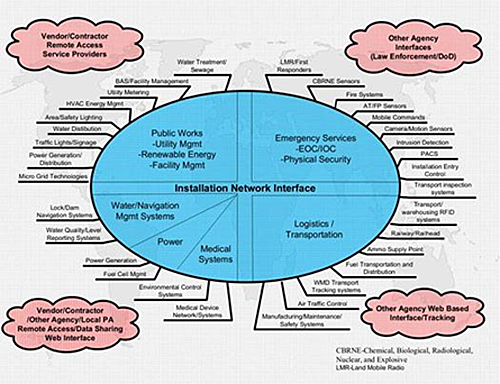
Figure 3: Examples of DoD OT and ICS Systems and Subsystems
Courtesy of Fred E. Abbitt, CISSP-ISSEP, CSSA / Physical and Control System Security SME, Information Systems Engineering Command, Information Assurance and Security Engineering Directorate
The majority of these systems were historically proprietary, analog, vendor supported, and used direct serial, and/or wireless connection, and were not IP enabled. The systems components such as Remote Terminal Units, Programmable Logic Controllers, Physical Access Control, Intrusion Detection Systems, CCTV, fire alarm systems, and utility meters have long equipment life spans, and are typically designated as Operational Technology (OT) and Real Property Equipment.
ICSs differ significantly from traditional administrative, mission support and scientific data processing information systems, and use specialized software, hardware and protocols. ICS systems are often integrated with mainstream organizational information systems to promote connectivity, efficiency, and remote access capabilities. The "front end" portions of these ICSs resemble traditional information systems in that they use the same commercially available hardware and software components. While the majority of an ICS system still does not resemble a traditional information system (IS), the integration of the ICS's "front end" with IS introduces some of the same vulnerabilities that exist in current networked information systems.
As these systems and components became digital and IP enabled, the interconnects to the organization network and business systems began to expose the organization to exploits and significant vulnerabilities. Typically, there was not a clear line of demarcation where one system started and one ended, for example a EMCS meter could be on the utility SCADA system, or on the buildings BAS. A comparison of IT versus OT systems is provided in the table below:
Table 1—IT vs. OT Systems Comparison
| Information Technology | Operational Technology | |
|---|---|---|
| Purpose | Process transactions, provide information | Control or monitor physical processes and equipment |
| Architecture | Enterprise wide infrastructure and applications (generic) | Event-driven, real-time, embedded hardware and software (custom) |
| Interfaces | GUI, Web browser, terminal and keyboard | Electromechanical, sensors, actuators, coded displays, hand-held devices |
| Ownership | CIO and IT | Engineers, technicians, operators and managers |
| Connectivity | Corporate network, IP-based | Control networks, hard wired twisted pair and IP-based |
| Role | Supports people | Controls machines |
ICSs can have long life spans (in excess of 20 years) and be comprised of technology that while functional, do not have the same technology refresh cycle as the IT. This introduces two issues: first, depending upon the relative age and isolation of the system, there may not be a patch or upgrade path for components of the system, and second, attempting to patch the component or employing modern scanning methods might disrupt the system. ICSs have experienced complete system shutdown when an intrusion detection system (IDS) or host-based scanning system (HBSS) scan is performed on an otherwise operational ICS. For an ICS, updates should be delayed until after a thorough analysis of deployment impact has been completed. This might stretch out security update timeliness and require flexibility in security control compliance measurement and enforcement.
An ICS physical system can span many miles; for example, locks and dams, pipelines, electric transmission and distribution systems can have many non-contiguous components, and there are a number of protocols commonly used by ICSs to allow the devices to communicate both horizontally and vertically. A building use could use a number of protocols at the same time. Typical building protocols are:
- LonWorks
- BACnet
- Modbus
- DNP 3
- Fox
These protocols were developed initially to ensure availability and reliability, and able to communicate down to the device level with small data transmission and verification. Many devices have embedded firmware with default passwords. The protocol organizations and vendors are now working to add additional security features on new systems while working on securing legacy systems.
Buildings can have a number of primary and secondary systems used to support the tenants and/or primary function of the building (office, hospital, warehouse, school, etc.).
Communications Network and Business Systems
The Communications Network and Business Systems include the Demarcation or Point of Entry where the external communications connect with the buildings internal network and include voice, data, video and multimedia information services, such as video conferencing and email. Typically the business systems are on a separate fiber high-speed backbone.
Building Management System (BMS)
The Building Management System provides automatic monitoring, interaction and management for electricity, ventilation, water supply, security and fire control to the building. A BMS typically manages the: Building Automation System (BAS), Electronic Security System (ESS), and the Fire and Life Safety System (FLS). For larger buildings and campuses, there will usually be a Building Operations Center (BOC), Security Operations Center (SOC), or Emergency Operations Center (EOC) that has engineering, O&M, security or emergency management personnel monitoring the BMS. In smaller buildings, there may only be a workstation and panels that alarm and report to an off-site BOC, SOC, or EOC.
Building Automation System (BAS)/Building Control System (BCS)
A building automation system (BAS) or Building Control Systems (BCS) is an example of a distributed control system. The control system is a computerized, intelligent network of electronic devices designed to monitor and control the mechanical, electronic, and lighting systems in a building. A building controlled by a BAS is often referred to as an Intelligent Building or a Smart Building.1
BAS core functionality keeps the building climate within a specified range, provides lighting based on an occupancy schedule, monitors system performance and device failures, and provides malfunction alarms (via email and/or text notifications) to building engineering/maintenance staff. The BAS functionality reduces building energy and maintenance costs when compared to a non-controlled building. The BAS typically consists of:
- Fire and Life and Safety (FLS)
- Physical Security and Access Control (PACS)
- Energy Management Systems (EMS), which includes Lighting Control
- Heating, Ventilation and Air Conditioning (HVAC)
A typical BAS architecture with multiple protocols is shown in Figure 4.
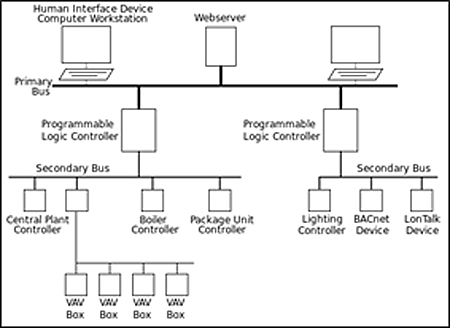
Figure 4: Typical BAS Architecture
Electronic Security System (ESSS)
The Electronic Security System (ESS) is critical for providing a secure environment and protecting the safety of tenants. Elements include: Anti-theft Security and Alarm System, Electronic Control System, Physical Access Control System, Closed-Circuit TV Surveillance System. The ESS is typically monitored by security personnel in the SOC.
Fire and Life Safety System (FLS)
The Fire and Life Safety (FLS) system consists of the fire alarms, sensors, sprinklers, smoke purge, and exhaust fans, and is often connected to the BAS to shutdown HVAC, elevators, and other equipment. The FLS typically connects to the local fire department and alarms in the SOC and BOC. Traditionally, these systems were in separate conduits and cabling went from the control panel to the devices.
Power over Ethernet
A new technology, Power over Ethernet (PoE)2, is changing the traditional cabling process and operations of the BMS. PoE describes any of several standardized or ad-hoc systems which pass electrical power along with data on Ethernet cabling. This allows a single cable to provide both data connection and electrical power to devices such as network hubs or closed-circuit TV cameras. Unlike standards such as Universal Serial Bus which also power devices over the data cables, PoE allows long cable lengths. Power may be carried on the same conductors as the data, or it may be carried on spare pairs of the cable. A BAS with PoE is shown in Figure 5.
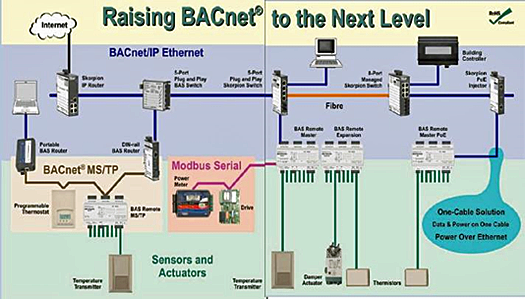
Figure 5: A BAS using Power over Ethernet
Credit: Contemporary Controls3
There are a number of new PoE devices and systems that are entering the market and addressing the cybersecurity of these systems will be a challenge. When legacy systems are being modernized and/or upgraded with PoE, understanding the network connections and ripple effects of loss of communications or power must be carefully analyzed as part of the Contingency Plan and Disaster Recovery/Business Continuity Plan.
Smart Buildings/Intelligent Buildings
A Smart Building or Intelligent Building project generally covers three key elements.4
- Communications Network and Office Automation
- Building Management System
- Integrated Services Infrastructure
The GSA Public Building Service (PBS) has been an active leader in the development of Smart Buildings. In March 2011, the PBS issued the Technology Policy for PBS-Owned Building Monitoring and Control Systems memo, with the objective to "converge the building's Monitoring and Control (M&C) systems infrastructure to enable smarter and more efficient operations." The GSA Smart Building concept is shown in Figure 6.
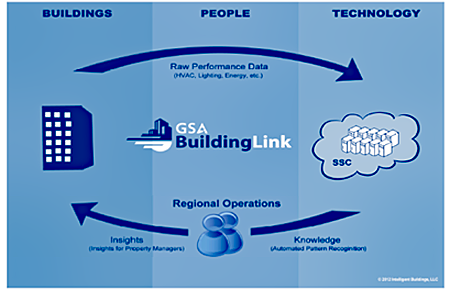
Figure 6: GSA Smart Buildings Concept
The GSA Smart Buildings effort had three broad objectives:
-
Open Communication Protocols—Non-proprietary building controls that give GSA greater building management flexibility and reduce service costs
-
Converged Control Systems Networks (IT backbone)—Elimination of unnecessarily redundant controls infrastructure such as conduit, cables, switches, and UPS's that will then allow interoperability and security compliance
-
Normalized Data for Systems Communications—Different controls manufacturers or even disparate systems can "talk" to each other allowing for data collection and analysis and more flexibility and management control
The resulting efforts are the convergence of the IT and OT into a new hybrid where the CIO provides the switches, routers and firewalls as Government Furnished Equipment (GFE), and all the building monitoring and control systems plug into the CIO fiber backbone in the distribution closet, as shown in Figure 7.
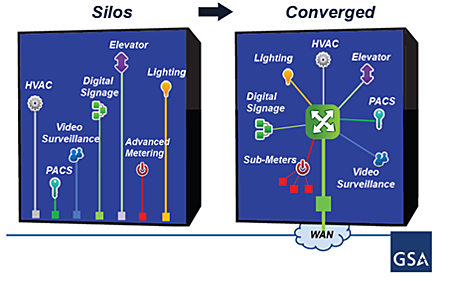
Figure 7: Converged Building M&C Connected in the Distribution Closet
While the GSA Smart Buildings model may work for many organizations, many others may not want to have the ESS or FLS running on the same fiber as the BAS. The redundancy and operational impact of converged systems is still a relatively new area.
To help evaluate system interdependencies, GSA has developed the Sustainable Facilities Tool. A sustainable building can operate more efficiently and cost less when the impacts of systems on each other are considered. The system bundling section can be leveraged to further understand whole building synergies and explore examples for ideas on what technologies might best be bundled together.
Achieving the design and operational performance requires a substantial change in mindset and training across multiple disciplines, changes in acquisition and contract language, and changes in the buildings operations and maintenance. GSA has developed a revised delivery process and is in the process of updating the Public Building Services Facilities Standard 100. The new process is shown in Figure 8.
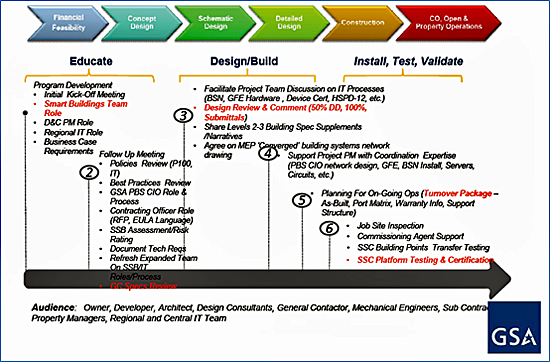
Figure 8: GSA Smart Buildings Life Cycle Approach
Smart buildings are now becoming the norm across the country, and as the buildings get ever smarter and interconnected with Smart Cars, Smart Cities, etc., they become vulnerable to outside attack and malware. As the IT and OT systems continue to converge, the need for new Cybersecurity skills and training for the facilities workforce will need to be developed.
The Department of Homeland Security Interagency Security Committee has developed several publications for risk assessments, facility security levels, and converged IT and OT assets, with an emphasis on physical access control systems, intrusion detection systems, and CCTV systems.
- The Risk Management Process for Federal Facilities: An Interagency Security Committee Standard , August 2013/1st Edition
- Facility Security Plan: An Interagency Security Committee Guide , February 2015/1st Edition
- Presidential Policy Directive 21 Implementation: An Interagency Security Committee White Paper , February 2015/1st Edition
- Securing Government Assets through Combined Traditional Security and Information Technology: An Interagency Security Committee White Paper , February 2015/1st Edition
Cyber-Physical Systems and the Critical Infrastructure Cybersecurity Framework
An emerging classification developed by the National Science Foundation and NIST is to classify the hybrid IT and OT as Cyber-Physical Systems (CPS), "Cyber-Physical Systems or "smart" systems are co-engineered interacting networks of physical and computational components. The Framework for Cyber-Physical Systems Release 1.0 was published May 2016.
These systems will provide the foundation of our critical infrastructure, form the basis of emerging and future smart services, and improve our quality of life in many areas. Cyber-physical systems will bring advances in personalized health care, emergency response, traffic flow management, and electric power generation and delivery, as well as in many other areas now just being envisioned. Other phrases that you might hear when discussing these and related CPS technologies include:
- Internet of Things (IoT)
- Industrial Internet
- Smart Cities
- Smart Grid
- "Smart" Anything (e.g., Cars, Buildings, Homes, Manufacturing, Hospitals, Appliances)
Source: https://www.nist.gov/el/cyber-physical-systems
CPS are defined as integrated, hybrid networks of cyber and engineered physical elements; co-designed and co-engineered to create adaptive and predictive systems, and respond in real time to enhance performance.5 CPS reflect the advances in technology, similar to the shift that occurred going from the Industrial Revolution/Physical Systems to the Internet Revolution/Cyber Systems, and now transitioning to Industrial Internet Revolution/Cyber Physical Systems as shown in Figures 9 and 10.
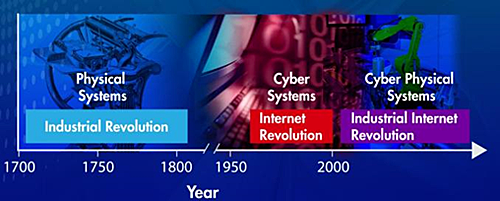
Figure 9: CPS Timeline Context
Credit: NIST Shyam Sunder Industrial Internet Workshop, March 2013
CPS are enabling a new generation of 'smart systems'. NIST has taken an active role and lead in defining the CPS and has held several workshops, resulting in several publications in early 2013:
- National Institute of Standards and Technology (NIST) Executive Roundtable on Cyber-physical Systems
- National Institute of Standards and Technology (NIST) Executive Roundtable on Cyber-physical Innovation
- National Institute of Standards and Technology (NIST) Executive Roundtable on Cyber-physical Systems Strategic R&D
- National Institute of Standards and Technology (NIST) Industrial Internet Workshop, The Industrial Internet and Cyber-Physical Systems: A Government Perspective
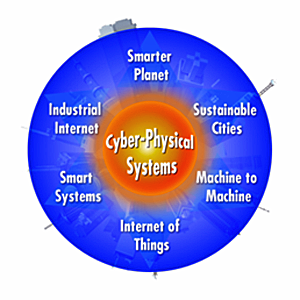
Figure 10: CPS Common Core Context
Credit: NIST Shyam Sunder Industrial Internet Workshop, March 2013
Essential CPS characteristics include:6
-
Cyber, engineered, and human elements as treated as integral components of a total system to create synergy and enable desired, emergent properties
-
Integration of deep physics-based and digital world models provides learning and predictive capabilities for decision support (e.g., diagnostics, prognostics) and autonomous function
-
Systems engineering-based open architecture and standards provide for modularity and composability for customization, systems of products, and complex or dynamic applications
-
Reciprocal feedback loops between computational and distributed sensing/actuation and monitoring/control elements enables adaptive multi-objective performance
-
Networked cyber components provide a basis for scalability, complexity management, and resilience
A comparison of the CPS systems and impacts across various sectors are provided in Table 2.
Table 2—Cyber-Physical Sector ContextWithin body use: 7
| Innovative Products or Applications | Cyber-Physical Systems | Impacts |
|---|---|---|
| Smart Manufacturing and Production | ||
| Agile manufacturing | Intelligent controls | Enhanced global competitiveness |
| Supply chain connectivity | Process and assembly automation | U.S.-based high tech manufacturing |
| Robotics working safely with humans | Greater efficiency, agility, and reliability | |
| Transportation and Mobility | ||
| Autonomous or smart vehicles (surface, air, water, and space) | Drive by wire vehicle systems | Accident prevention and congestion reduction (zero-fatality highways) |
| Vehicle-to-vehicle and vehicle-to-infrastructure communication | Plug ins and smart cars | Greater safety and convenience of travel |
| Interactive traffic control systems | ||
| Next-generation air transport control | ||
| Energy | ||
| Electricity systems | Smart electric power grid | Greater reliability, security, and diversity of energy supply |
| Renewable energy supply | Plug-in vehicle charging systems | Increased energy efficiency |
| Oil and gas production | Smart oil and gas distribution grid | |
| Civil Infrastructure | ||
| Bridges and dams | Active monitoring and control system | More safe, secure, and reliable infrastructure |
| Municipal water and wastewater treatment | Smart grids for water and wastewater | Assurance of water quality and supply |
| Early warning systems | Accident warning and prevention | |
| Healthcare | ||
| Medical devices | Wireless body area networks | Improved outcomes and quality of life |
| Personal care equipment | Assistive healthcare systems | Cost-effective healthcare |
| Disease diagnosis and prevention | Wearable sensors and implantable devices | Timely disease diagnosis and prevention |
| Buildings and Structures | ||
| High performance residential and commercial buildings | Whole building controls | Increased building efficiency, comfort and convenience |
| Net-zero energy buildings | Smart HVAC equipment | Improved occupant health and safety |
| Appliances | Building automation systems | Control of indoor air quality |
| Networked appliance systems | ||
| Defense | ||
| Soldier equipment | Smart (precision-guided) weapons | Increased warfighter effectiveness, security, and agility |
| Weapons and weapons platforms | Wearable computing/sensing uniforms | |
| Supply equipment | Intelligent, unmanned vehicles | Decreased exposure for human warfighters and greater capability for remote warfare |
| Autonomous and smart underwater sensors | Supply chain and logistics systems | |
| Emergency Response | ||
| First responder equipment | Detection and surveillance systems | Increased emergency responder effectiveness, safety, efficiency, and agility |
| Communications equipment | Resilient communications networks | Rapid ability to respond to natural and other disasters |
| Fire-fighting equipment | Integrated emergency response systems | |
NIST has developed a reference architecture shown in Figure 11 that:
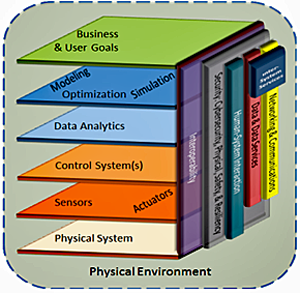
Figure 11: CPS Reference Architecture
- Provides a common lexicon and taxonomy that can apply across CPS
- Shows a common architectural vision to help facilitate interoperability between components and systems
- Enables creation of reusable CPS components and tools to measure and evaluate their performance
- Promotes communication across diverse stakeholder community
- Provides a common lexicon and taxonomy that can apply across CPS
- Shows a common architectural vision to help facilitate interoperability between components and systems
- Enables creation of reusable CPS components and tools to measure and evaluate their performance
- Promotes communication across diverse stakeholder community
The use of the CPS terminology and reference architecture will continue to be an evolving area.
National Institute of Standards and Technology Computer Security Resource Center
The NIST Computer Security Division, Computer Security Resource Center is where the standards and publications are maintained. NIST 800-53 Recommended Security Controls for Federal Information Systems and Organizations, and NIST 800-82 Guide to Industrial Control Systems (ICS) Security are used by most federal agencies as the baseline to evaluate their systems. Both publications were updated and published in spring 2013.
The STUXNET, FLAME, and other cyber attacks have shown how vulnerable the nation's ICS are. As the Smart Grid develops, enhanced security controls are being developed by NIST, to include the NISTIR 7628 Guidelines for Smart Grid Cyber Security, and the NIST Framework and Roadmap for Smart Grid Interoperability Standard, Release 2.0. Buildings that have Advanced Smart Metering and other web or wireless connections to the system should be secured and tested to ensure vulnerabilities are mitigated and risks minimized.
NIST Global City Teams Challenge and NIST Cybersecurity for IoT Program
The Global City Teams Challenge (GCTC) program is a collaborative platform for the development of smart cities and communities, led by National Institute of Standards and Technology, a bureau of U.S. Department of Commerce, in partnership with other U.S. federal agencies including U.S. Department of Homeland Security Science and Technology Directorate (DHS S&T), National Science Foundation, International Trade Administration, and National Telecommunications and Information Administration. It enables local governments, nonprofit organizations, academic institutions, technologists, and corporations from all over the world to form project teams, or "action clusters," and "SuperClusters," to work on groundbreaking Internet of Things (IoT) and Cyber-Physical Systems (CPS) applications within the city and community environment.
NIST's Cybersecurity for the Internet of Things (IoT) program supports the development and application of standards, guidelines, and related tools to improve the cybersecurity of connected devices and the environments in which they are deployed. By collaborating with stakeholders across government, industry, international bodies, and academia, the program aims to cultivate trust and foster an environment that enables innovation on a global scale.
Department of Homeland Security ICS-CERT
The Department of Homeland Security Control Systems Security Program is part of the United States Computer Emergency Readiness Team (US-CERT) and provides tools, standards, training, and publications for ICS.
The Industrial Control Systems Cyber Emergency Response Team (ICS-CERT) works to reduce risks within and across all critical infrastructure sectors by partnering with law enforcement agencies and the intelligence community and coordinating efforts among Federal, state, local, and tribal governments and control systems owners, operators, and vendors. Additionally, ICS-CERT collaborates with international and private sector Computer Emergency Response Teams (CERTs) to share control systems-related security incidents and mitigation measures.
Similar to the advancement of the number of malicious malware and hacking of traditional IT systems, critical infrastructure (CI) is now a primary target and the number of ICS-CERT reported incidents is exponentially increasing.
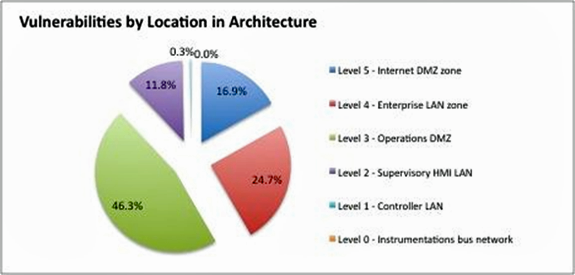
Figure 12: ICS Vulnerabilities reported to ICS-CERT by ISA 99 Layer
CSET is a desktop software tool that guides users through a step-by-step process to assess their control system and information technology network security practices against recognized industry standards. The output from CSET is a prioritized list of recommendations for improving the cybersecurity posture of the organization's enterprise and industrial control cyber systems. The tool derives the recommendations from a database of cybersecurity standards, guidelines, and practices. Each recommendation is linked to a set of actions that can be applied to enhance cybersecurity controls.

Figure 13: DHS Cyber Security Evaluation Tool
CSET has been designed for easy installation and use on a stand-alone laptop or workstation. It incorporates a variety of available standards from organizations such as National Institute of Standards and Technology (NIST), North American Electric Reliability Corporation (NERC), International Organization for Standardization (ISO), U.S. Department of Defense (DoD), and others. When the tool user selects one or more of the standards, CSET will open a set of questions to be answered. The answers to these questions will be compared against a selected security assurance level, and a detailed report will be generated to show areas for potential improvement.
CSET provides an excellent means to perform a self-assessment of the security posture of your control system environment.
GRASSMARLIN ICS Network Discovery Tool
In support of a passive means to generate an Industrial Control System network and discover IP devices, NSA has developed the GRASSMARLIN (GM) tool. GRASSMARLIN is a software prototype that provides a method for discovering and cataloging SCADA (Supervisory Control and Data Acquisition) and ICS (Industrial Control System) systems on IP-based networks. GRASSMARLIN uses a variety of sources to generate this data, including PCAP files, router and switch configuration files, CAM tables and live network packet captures. The tool can automatically determine the available networks and generate the network topology as well as visualize the communication between hosts. GRASSMARLIN is still in a prototype phase.
Grassmarlin has been approved for Open Source distribution. The executables and documentation can be accessed via the links below.
Release Notes: https://github.com/iadgov/GRASSMARLIN
Download: https://github.com/iadgov/GRASSMARLIN/releases/tag/v3.0.0
The GM POC is Jerome Crocker
A GM Plug-In has been integrated into the DHS ICS-CERT Cyber Security Evaluation Tool (CSET). When installing the tool, use Custom Install and select the GM Plug-In option. If you need assistance and/or technical support with CSET and GM Plug-In, contact Barry Hansen or Michael Chipley.
Advanced Control System Tactics, Techniques, and Procedures (TTPs)
USCYBERCOM developed the Advanced Control System Tactics, Techniques, and Procedures (TTPs) that provide detailed step-by-step guidance to respond to a cyber attack. The starting point is to develop the Fully Mission-Capable (FMC) Baseline which consists of documentation that characterizes the control system such as the Topology diagram, Enclave entry points, User accounts, Server/workstation documentation, and Network documentation.
The Recovery Jump-Kit contains the tools the control systems team and IT team will need to restore a system to its last FMC state during Mitigation and Recovery. Knowing what the Recovery point should be is the key to ensuring all known remnants of an attack have been removed from all components of the control system. In addition to containing the operating software for all devices, the Jump-Kit it also contains the software hashes of the devices on the network and the firmware and software updates for all system devices and checksums and hashes are in conformance with vendor specifications, and all hardware and software are configured in accordance with operational requirements. During Recovery, the Jump-Kit is utilized to reimage the firmware/software operating on the affected devices.
Department of Homeland Security Science and Technology
DHS S&T has developed several tools to assess the risk and resiliency of buildings, to include the cyber threat. The Integrated Rapid Visual Screening Tool, and the Owners Performance Requirement Tool assist building owners and operators evaluate the threats, vulnerabilities, and consequences and compare mitigation options.
Committee for National Security Systems ICS Overlay
The CNSS provides a forum for the discussion of policy issues, and is responsible for setting national-level Information Assurance policies, directives, instructions, operational procedures, guidance, and advisories for U.S. Government (USG) departments and agencies for the security of National Security Systems (NSS).
In April 2012, DoD formed a Technical Working Group (TWG) and undertook the task of creating the first CNSSI 1253 ICS-PIT Overlay:
"Security control overlays are specifications of security controls and supporting guidance used to complement the security control baselines and parameter values in the Committee on National Security Systems Instruction (CNSSI) No. 1253 and to complement the supplemental guidance in the NIST SP 800-53. Organizations select and apply CNSSI No. 1253 security control overlays by using the guidance in each of the standardized, approved and CNSS-published overlays."
The TWG delivered the first ICS-PIT Overlay to the CNSS in January, 2013, after extensive collaboration among 65 representatives spanning DoD, DHS and numerous agencies. The Overlay is both a "primer," with a standard architecture and layers diagram, and a pictorial of typical devices, sensors and actuators that enable the I&E, IT and Information Assurance (IA) staff in the field to identify and understand the operational protocols (Modbus, LonTalk, etc.), network ports, and connections.
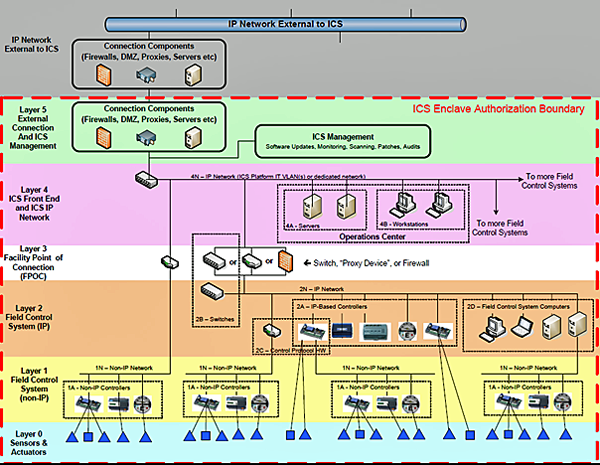
Figure 14: CNSSI 1253 ICS Overlay Enclave Authorization Boundary and Layers
The initial ICS-PIT Overlay was DoD-centric and used DoD specific parameters, and was issued as an informational and training document, and was included in the CSET 5.1 release. About the same time, working with the NIST SP 800-82R2 writing team, much of the material from the CNSSI ICS Overlay was incorporated into the update to 800-82, to include the new section 2.5 Other Types of Control Systems. With the release of NIST 800-53 R4 and NIST SP 800-82 R2, the CNSSI ICS Overlay is now obsolete and should not be used.
Handbook for Self-Assessing Security Vulnerabilities & Risks of Industrial Control Systems on DoD Installations
This handbook was developed by the Air Force 346th Test Squadron, 262nd Network Warfare Squadron, Idaho National Laboratory and other stakeholder agencies in response to the need to address the lack of field guidance for ICS cybersecurity. The Department of Defense (DoD) Components and Agencies are encouraged to use this handbook to help establish a risk management framework to identify and prioritize mission-related vulnerabilities and risks that may be exposed or created by network connectivity to Industrial Control Systems (ICS). Installations & Environment (I&E)-related ICS include computer hardware, software, and associated sensors and controllers used to monitor and/or control real property, such as on-installation electricity, water, wastewater, natural gas, airfield lighting and petroleum systems. It also includes building heating and air conditioning equipment, lighting, fire and life safety systems. Supervisory Control and Data Acquisition Systems (SCADA), Distributed Control Systems (DCS), Energy Management Control Systems (EMCS) are also types of ICS.
Footprinting/Discovery
There are many tools and methods that can be used to identify building control systems that are exposed on the internet. One of the most powerful is Shodan. Figure 15 illustrates a search for Tridium which shows the IP address, protocol, organization, location, application software, firmware and other details. Figure 16 illustrates a search for Distech, which shows the building controller connecting through the Tridium servers and also displays the devices ID's, operating system, MD5 Hash, and Host ID's.
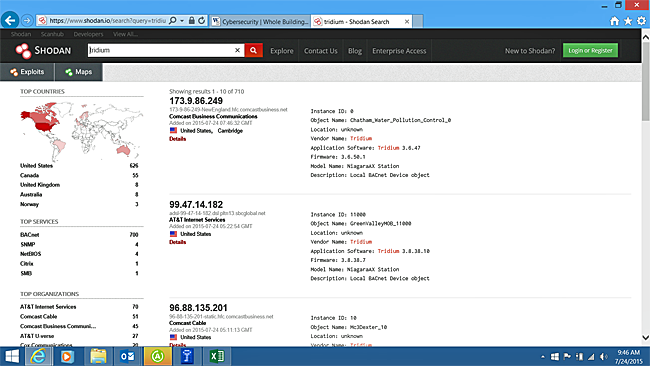
Figure 15: Shodan Search Results for Tridium Products
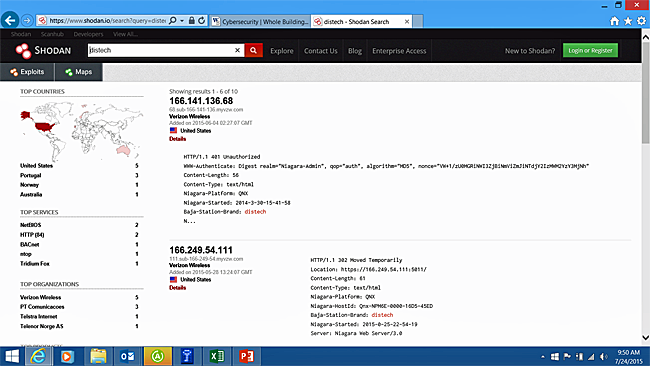
Figure 16: Shodan Search Results for Distech Products
In the majority of these cases, clicking on the IP will open the login to the operator console as shown in Figure 17. In many cases, the browser is using an unencrypted http port 80, rather than encrypted https port 443, meaning the login credentials are being sent as open text across the internet. Organizations should not expose their Building Control Systems to direct internet connections; they should be in a DMZ, separated from the IT systems, and require a VPN connection.
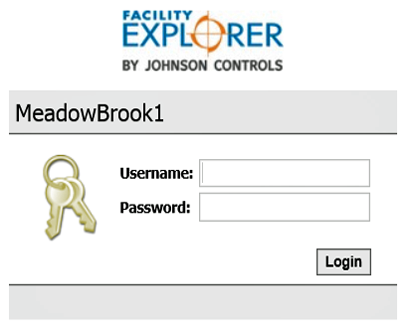
Figure 17: Direct Internet Connection to Johnson Controls Facility Explorer Login
Other tools include Wireshark, NSA GrassMarlin, SamuraiSTFU, Kali Linux, NexDefense Sophia, GlassWire, Snort, Gleg, and Digital Bond Bandolier.
Additional Resources
Federal Agencies With Control Systems Responsibilities or Capabilities
- Air Force Civil Engineering Center
- Army Installation Management Command
- Department of Defense Environmental Security and Technology Accreditation Program
- Department of Defense Installation Energy Office
- Department of Energy
- Department of Energy Grid—Interactive Efficient Buildings
- Defense Threat Reduction Agency
- Defense Information Security Agency
- Department of Homeland Security Critical Infrastructure Agency
- Department of Homeland Security ICS Threats and Alerts
- Department of Homeland Security Interagency Security Committee
- Department of Homeland Security National Cybersecurity and Communications Integration Center's (NCCIC)
- General Services Administration Public Buildings Service
- Lawrence Berkeley Lab Building Technology and Urban Systems
- National Renewable Energy Laboratory
- National Security Agency
- Naval Facilities Engineering Command
- North American Electrical Reliability Corporation
- Pacific Northwest National Laboratory
- USACE Cyber Center of Expertise
- USCYBERCOM
Control System Cyber Threats
- Black Energy
- BrickerBot
- CRASHOVERRIDE, aka, Industroyer
- Duqu
- Flame
- Havex
- Meltdown and Spectre
- Operation Cleaver
- Operation Dust Storm
- Petya
- Shamoon
- Stuxnet
- WannaCry
Publications
- Air Force Guidance Memorandum, Civil Engineer Control Systems Cybersecurity , 2017.
- BOMA "Cybersecuring Your Building Control Systems and Property", June 2016.
- Code of Practice for Cyber Security in the Built Environment, The Institution of Engineering and Technology, December 2014.
- Committee for National Security Systems Instruction 1253—Security Categorization and Control Selection for National Security Systems
- CoreNet "Cybersecuring Building Control Systems" , April 2015.
- Cybersecurity for Hospitals and Healthcare Facilities: A Guide to Detection and Prevention, September 2016.
- Cyber-Security Glossary (Ayala), September 2015 [available on Amazon]
- DCIO GIAC GICSP Approval Memo , 2017.
- DoD Advanced Control Systems Tactics, Techniques and Procedures , DHS ICS JWG Fall meeting, September 2016.
- Department of Defense Instruction 8500.01 Cybersecurity , March 2014.
- Department of Defense Instruction 8510.01 Change 1 Risk Management Framework (RMF) for DoD Information Technology (IT) , May 2016.
- Department of Defense Instruction 8530.01 Cybersecurity Activities Support to DoD Information Network Operations , March 2016.
- Department of Defense 8500.1 Information Assurance
- Department of Defense 8570M Information Assurance Workforce Improvement Program
- Department of Defense Cloud Computing Security Requirements Guide , Version 1, Release 1, January 2015.
- Department of Defense Directive 8140.01 Cyberspace Workforce Management , August 11, 2015.
- Department of Defense Handbook for Self-Assessing Security Vulnerabilities & Risks of Industrial Control Systems on DoD Installations , 2012.
- Department of Defense and General Services Administration Improving Cybersecurity and Resilience through Acquisition
- Department of Defense Advanced Control System Tactics, Techniques, and Procedures (TTPs), Revision 1 , 2017.
- Department of Defense Mission Assurance Vulnerability Assessment Benchmarks, JMAA 2014 (FOUO document)
- Department of Homeland Security Cyber Security Procurement Language for Control Systems
- Department of Homeland Security Cybersecurity Evaluation Tool
- FacilitiesNet "The Power and Convenience of Networked BAS Come With Cybersecurity Concerns As Well", July 2016.
- Facility Security Plan: An Interagency Security Committee Guide , February 2015/1st Edition.
- Federal Facility Cybersecurity, GAO 15-6, December 2014, Government Accountability Office.
- Framework for Cyber-Physical Systems Release 1.0
- GovTechWorks New Facilities Promise 'Smart' Tech—But Can They Keep Hackers Out?
- Industrial Internet Consortium (IIC) Industrial Internet Security Framework (IISF) , September 2016.
- National Academies of Science Federal Facilities Council "Cybersecurity Building Control Systems—Exploiting controls systems demonstration using Shodan, DB Exploit, Google Hacking, Diggity, Kali Linux", March 2015.
- National Institute of Standards and Technology NISTIR 6392 GSA Guide to Specifying Interoperable Building Automation and Control Systems Using ANSI/ASHRAE Standard 135-1995, BACnet
- National Institute of Standards and Technology SP 800-53 Rev 4 Security and Privacy Controls for Federal Information Systems and Organizations
- National Institute of Standards and Technology SP 800-82 Guide to Industrial Control Systems (ICS) Security , June 2011.
- National Institute of Standards and Technology SP 800-82 Rev 2 Guide to Industrial Control Systems (ICS) Security , May 2015.
- National Institute of Standards and Technology SP 800-137 Information Security Continuous Monitoring (ISCM) for Federal Information Systems and Organizations , September 2011.
- National Institute of Standards and Technology SP 800-160 Systems Security Engineering An Integrated Approach to Building Trustworth Resilient Systems , May 2014.
- National Institute of Standards and Technology SP 800-171 Protecting Controlled Unclassified Information in Nonfederal Information Systems and Organizations , June 2015.
- NextGov "The Internet of Things Means Hospitals Are More Hackable Than Ever. The VA is Prepared", March 2016
- NIBSJ "Cybersecuring Building Control Systems" , October 2015.
- NIBSJ "Cybersecuring Healthcare Building Control Systems" , August 2016.
- North American Electric Reliability Corporation Critical Infrastructure Protection Standards
- Overview of the DoD Risk Management Framework and the Committee for National Security Systems Instruction 1253, Industrial Control Systems Platform IT Overlay
- Presidential Policy Directive 21 Implementation: An Interagency Security Committee White Paper , February 2015/1st Edition,
- Retrofit Magazine "CYBERSECURING Building Control Systems", April 2016.
- SANS ICS Summit 2014 "Cybersecuring DoD Industrial Control Systems" , February 2014.
- SANS ICS Summit 2015 "Cybersecuring DoD Industrial Control Systems, One Year Later" , February 2015.
- Securing Government Assets through Combined Traditional Security and Information Technology: An Interagency Security Committee White Paper , February 2015/1st Edition.
- The Leader Magazine—CoreNet Global, "Are your building-control systems secure against cyber attack?", March 2016.
- The Risk Management Process for Federal Facilities: An Interagency Security Committee Standard , August 2013, 1st Edition.
- Today's Facility Manager "FM Issue: Cybersecurity Evolution", March 2014.
- UBM's Future Cities "Target Breach: A Warning for 'Dumb' Smart Buildings", February 2014.
- UFC 4-010-06 Cybersecurity of Facility-Related Control Systems, September 2016.
- UFGS 25 10 10 Utility Monitoring and Control Systems (UMCS) Front End and Integration, November 2015
- UFGS 25 10 10.00 24 ICS Front End Integration (NAVFAC) , May 2013.
- Wall Street Journal "Federal Government Networks Vulnerable to Hackers Through Building Systems, Report Warns", January 2015.
General Industry IT and OT Tools
- Bishop Fox Diggity
- Brett Shavers RegRipper
- ControlThings I/O
- Department of Homeland Security Science and Technology Building and Infrastructure Protection Series Tools
- Department of Homeland Security Science and Technology Integrated Rapid Visual Screening Tool
- Department of Homeland Security Science and Technology Owner Performance Requirements Tool
- GlassWire Firewall
- GrassMarlin
- Kali Linux
- Host Identity Protocol
- Lookout
- Malware Bytes
- Microsoft Enhanced Mitigation Experience Tool
- Microsoft Sysinternals Autorun
- Microsoft Sysinternals Process Explorer
- Microsoft Sysinternals Process Monitor
- Passmark OSForensics
- Passive Optical Networks
- Qualys
- Schwietzer Engineering Labs acSELerator
- Shodan
- SiteLock
- Webroot
- VirusTotal
- Yara
Building and Control System Vendors/Products
- Armis
- Bedrock Automation
- Cisco Umbrella
- CyberX
- Delta Controls
- Dragos CyberLens
- FEND
- FoxGuard Solutions
- Honeywell Building Solutions
- Indegy
- Johnson Control Systems
- IPERC
- Lynx CyberPro
- Mocana
- Onclave Secure IoT
- Open Automation Software
- OSI Soft
- Owl
- PAS Global
- Symantec (now a division of Broadcom)
- Tellabs
- Tempered Networks
- Teneable
- Tofino Security
- Tridium
- Tripwire
- Ultra3eTI
- Vericlave
- Waterfall
- WESCO
Websites
- Committee for National Security System (CNSS)
- Department of Defense Cybersecurity
- Department of Defense CIO Knowledge Service Energy, Installations and Environment Control Systems (requires CAC)
- Defense Industrial Base Information Assurance Program
- Department of Homeland Security ICS-CERT
- Department of Homeland Security Science and Technology
- Department of Homeland Security National Protection and Programs Directorate
- General Services Administration Smart Buildings
- Industrial Control Systems Information Sharing and Analysis Center
- ISA99 Committee on Industrial Automation and Control Systems Security
- National Institute of Standards and Technology Cybersecurity Framework
- North American Electric Reliability Corporation
- SANS ICS Security
- Smart Power Infrastructure Demonstration for Energy Reliability and Security (SPIDERS)
- University of York – Introduction to Cyber Security and Data Protection
- USCYBERCOM
- Wikipedia List of Automation Controls
Protocols
Training Courses
- Advanced Cybersecuring Building Control Systems
- Best Trade Schools—Cybersecurity Programs
- Certified Information Security Professional (CISSP)
- Certified Cyber Forensics Professional (CCFP)
- Computer Science—Online Degree Opportunities Overview
- Computer Science Scholarships and Financial Aid
- ComputerScienceMS.com
- Cyber Degrees.org
- Cyber Security—Online Degrees and Opportunities
- Cybersecuring DoD Control Systems
- Defensive Counter Cyber Operator—Identify
- Defensive Counter Cyber Operator—Hunt
- Department of Defense Enterprise Mission Assurance Support Service (EMASS)
- Department of Homeland Security ICS-CERT Training Courses
- DHS National Initiative For Cybersecurity Careers and Studies
- Federal Virtual Training Environment
- Introduction To Cybersecuring Building Control Systems
- Online Computer Science Degree Options for Engineers
- Online Masters in Computer Science
- SANS ICS Security Courses
- Web Development—Online Degree Options
- Your Building Control Systems Have Been Hacked, Now What? Tactics, Techniques and Procedures Workshop
Workshops
- "Cybersecurity of Buildings Workshop" – Jan. 28, 2014
Focus was on the recently released draft DHS ISC Converged Systems White Paper document, GSA Smart Buildings program, and the NIST SP 800-82 Guide to Industrial Control Systems Security. This workshop built on the Cybersecurity of Building track listed below. The purpose of the Workshop was to bring the engineering, security, IT and IA communities together to build on current initiatives to create a common architecture and joint publications to develop defense in depth, continuous monitoring, incident response and recovery, and information sharing CONOPS for ICS and Converged Systems. Download materials and presentations. - "Cybersecurity of Buildings Workshop: OT and IT Convergence—A New Paradigm". Building Innovation 2014: The National Institute of Building Sciences Annual Conference & Expo – Jan. 6, 2014.
- "Cybersecuring Facilities and Facilities Systems". National Academy of Sciences (NAS) Federal Facilities Council (FFC) – May 2015.
Footnotes
1 [http://en.wikipedia.org/wiki/Building_automation]
2 [http://en.wikipedia.org/wiki/Power_over_Ethernet]
3 [Raising BACnet® to the Next Level, Connecting BACnet Devices to an IP Infrastructure ]
4 [xinca.com/ elements-intelligent-buildings- 2734. html]
5 [Key metrics include: efficiency and sustainability, agility and flexibility, reliability and resilience, safety and security.]
6 [National Institute of Standards and Technology (NIST) Executive Roundtable on Cyber-physical Systems]
7 [NIST Shyam Sunder Industrial Internet Workshop, March 2013]








